I had my chance to play with JavaFX and its samples. Wow ! unbelievably cool stuff and JavaFX raises the bar for other RIA API tools. In my experience, JavaFX eats AJAX and other RIA scrApting tools for lunch !
- JavaFX offers an easy to understand declarative API for building RIA applications that can include Media, Graphics, XML Web Services and also plugging Java libraries.
- Comparing to Abobe Flex (esp. MXML) and Microsoft SilverLight, JavaFX Script is much simpler and easier to learn for any budding RIA developer.
- Netbeans 6.5 provides terrific JavaFX development capabilities for edit/code completion/compile/run/deploy JavaFX apps.
- JavaFX Deploys as a Java client application distributed via Java Web Start/JNLP running on existing Java environment.
- JavaFX builds on JNLP Security, a very rugged and proven solution – than dubious AJAX security.
JavaFX and JNLP Security
JavaFX uses the Java Network Launch protocol (JNLP), which provides a standard way for packaging and  provisioning the JavaFX applications and then launching JavaFX applications from a client environment. Typically JavaFX apps are started from a Web browser using Java Web Start (JWS) runtime environment (bundled as part of JRE), that downloads, caches, and then executes the JavaFX application locally.
provisioning the JavaFX applications and then launching JavaFX applications from a client environment. Typically JavaFX apps are started from a Web browser using Java Web Start (JWS) runtime environment (bundled as part of JRE), that downloads, caches, and then executes the JavaFX application locally.
Typical to any other stand-alone Java application, JavaFX applications launched using JWS runs outside a Web browser using the sandbox features of the underlying Java runtime platform. JWS also allows defining security attributes for client-side Java applications and their access to local resources, such as file system access, making network connections, and so on. These security attributes are specified using XML tags in the JNLP descriptor(.jnlp) file. The JNLP descriptor defines the application access privileges to the local and network resources. In addition, JWS allows the use of digital signatures for signing JAR files in order to verify the application origin and its integrity so that JavaFX applications can be trusted before it is downloaded to a client machine. The certificate used to sign the JAR files is verified using the trusted certificates in the client keystore. This helps users avoid starting malicious applications and inadvertent downloads without knowing the originating source of the JavaFX application. Signing a JavaFX application is quite similar to the steps involved in signing a JAR file or an Applet.
The JNLP descriptor file is an XML-based document that describes the application classes (JAR files), their location in a Web server, JRE version, and how to launch JavaFX application in the client environment. The client user downloads the JNLP file from the server, which automatically launches the JavaFX application on the client side. The JNLP file uses XML elements to describe the deploued JavaFX application. The root element is tagged as <jnlp>, which contains the four core sub-elements: information, security, resources, and application-desc. To enforce security, the <security> element is used to specify the required permissions. The security element provides two permission options: <all-permissions/> to provide an application with full access to the client’s local computing resources, and <j2ee-application-client-permissions/> to provide a selected set of permissions that includes socket permissions, clipboard access permission, printing permission, and so forth.
Here is a sample JNLP descriptor I played with the security constraints of a sample JavaFX application:
<?xml version=”1.0″ encoding=”utf-8″?>
<jnlp spec=”1.5+” codebase=”http://www.example.com/HelloWebStartJFX/” href=”HelloWebStartJFX.jnlp”>
<information>
<title>Hello Web Start JFX</title>
<vendor>John Doe</vendor>
<homepage href=”http://www.example.com/HelloWebStartJFX/”/>
<description>Web Start example for JavaFX Scripts</description>
<offline-allowed/>
</information>
<security>
<j2ee-application-client-permissions/>
</security>
<resources>
<j2se version=”1.5+” href=”http://java.sun.com/products/autodl/j2se”>
</j2se>
<jar href=”javafxrt.jar” main=”true”/>
<jar href=”swing-layout.jar”/>
<jar href=”HelloWebStartJFX.jar”/>
</resources>
<application-desc main-class=”net.java.javafx.FXShell”>
<argument>HelloWebStart</argument>
</application-desc>
</jnlp>
To learn more, test-drive the JavaFX code and samples.
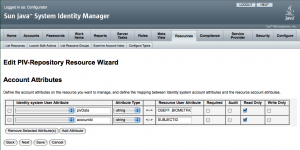
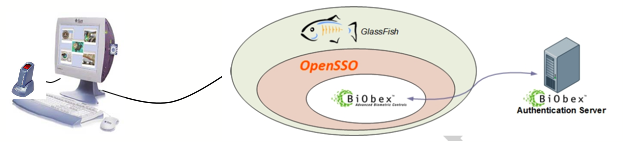
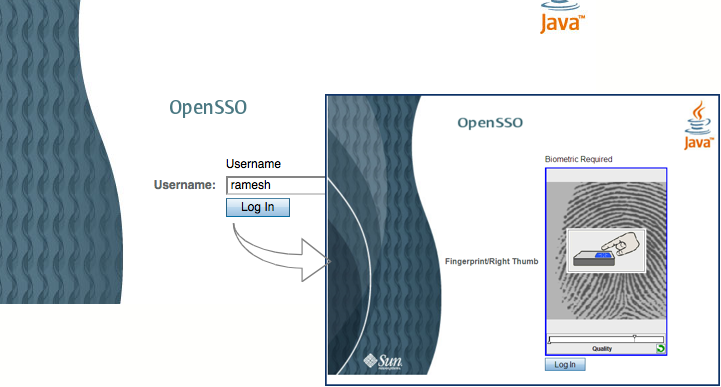
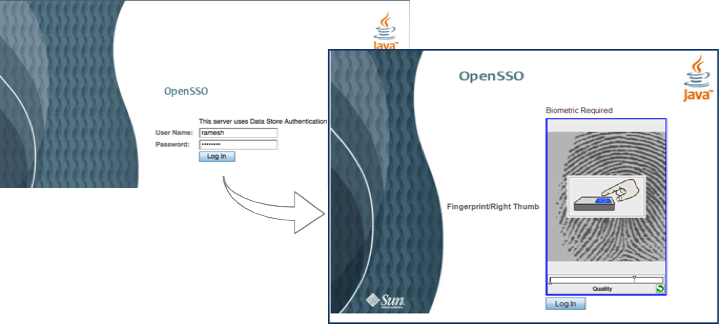
 long-time buddy of mine organized this event at one of the Hartford skyscrappers – What a great view ! I had contributed code artifacts to OWASP projects before, but it was the first time I had a chance to attend an OWASP event. Amazing to see..it was an enthusiastic crowd with a lot of focus on the emerging trends in IT security. I took a small piece of the IT puzzle.. to present a topic on “Multi-factor Authentication” and then a demo showing OpenSSO w. PKI/Biometric authentication. It was a well-organized event and I saw a lot of interests around OpenSSO.
long-time buddy of mine organized this event at one of the Hartford skyscrappers – What a great view ! I had contributed code artifacts to OWASP projects before, but it was the first time I had a chance to attend an OWASP event. Amazing to see..it was an enthusiastic crowd with a lot of focus on the emerging trends in IT security. I took a small piece of the IT puzzle.. to present a topic on “Multi-factor Authentication” and then a demo showing OpenSSO w. PKI/Biometric authentication. It was a well-organized event and I saw a lot of interests around OpenSSO.

 of Massachusetts) at an
of Massachusetts) at an