Since inception, I had been following MITRE’s ATT&CK Navigator knowledge base for studying (threat modeling) pre and post-exploit techniques on Web, Mobile and Enterprise applications more particularly running on Windows and Linux systems. Indeed, it is a great resource for understanding the devil in the details of attack techniques and simulate it from simple hacking credentials from the initial access to exfiltration and till command & control. You can study and understand how adversaries launch and execute attacks and evolve a defense strategy based on the threats we potentially face.
MITRE announced the version 2 of the ATT&CK Navigator last week (l believe last week of May 2018).
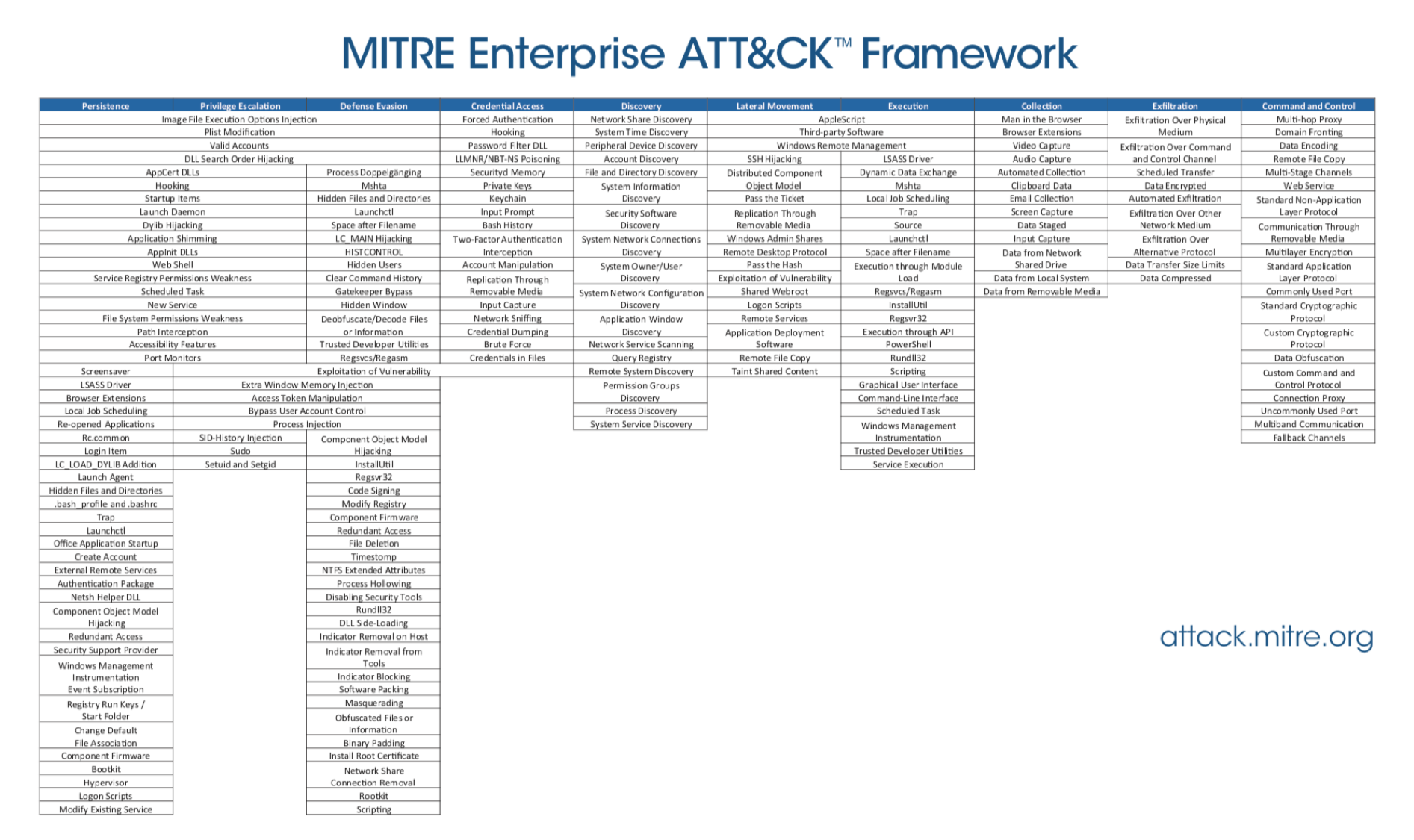
MITRE Enterprise ATT&CK Framework for Cyber Threat Intelligence
To try and review each layer and define your custom attack matrix, you can interactively create layers within the Navigator or programmatically and then visualized via the Navigator.
For accessing Navigator from your browser:
https://mitre.github.io/attack-navigator/enterprise/
For accessing Navigator using Mobile:
https://mitre.github.io/attack-navigator/mobile/
Check out these URLs of ATT&CK Matrix for Linux, Windows, Mac….Will post more details on how to simulate an attack… soon.