Another winter storm hit us yesterday… this time we had up to 12″ of snow – My back hurts after blowing and shoveling up my huge driveway. This week supposed to be the most busiest Christmas shopping day, but this storm may put another dent on already slagging retail sales !
NSA probes into Microsoft .NET framework :-)
Few weeks ago, I picked this document from one of my crazy mailing list subscriptions – Surprising to note an email, that featured an NSA  UNCLASSIFIED document that digs deep into Security features of Microsoft .NET Framework ( versions 1.0, 1.1 and 2.0). The document is a bit dated and it did’nt highlight the latest security features of .NET version 3.x or above. The summary of the document is quite interesting… “Because the security configuration of the .NET Framework depends on the interplay between the operating system security settings, the operating environment of the host, and the nature of the software that is required or available for execution on the host, it does not lend itself …….“.
UNCLASSIFIED document that digs deep into Security features of Microsoft .NET Framework ( versions 1.0, 1.1 and 2.0). The document is a bit dated and it did’nt highlight the latest security features of .NET version 3.x or above. The summary of the document is quite interesting… “Because the security configuration of the .NET Framework depends on the interplay between the operating system security settings, the operating environment of the host, and the nature of the software that is required or available for execution on the host, it does not lend itself …….“.
Microsoft .NET is not my forte, but the summary implied me that Microsoft .NET has to inherit the known weaknesses of Microsoft Windows OS ! . I was also curious to know their suggestions to XML Web services security with .NET – it was absent in the document as it hardly touched on Web services.
It’s been a while I used a Windows machine 🙂 No offense, I may be wrong on my comments or need a bit more .NET education . Overall, it is an impressive document with quite a lot of recommendations and best practices (for any budding developer) involved with securing .NET environment.
To read more on NSA’s recommendations to Microsoft .NET security, refer to: http://www.nsa.gov/snac/app/I731-008R-2006.pdf
Match-to-SmartCard PKI and Biometric authentication.
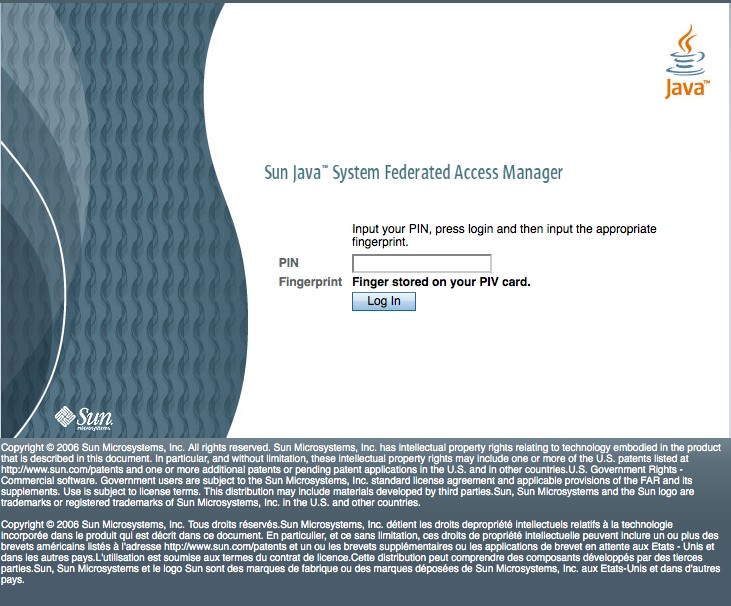 A picture is worth a thousand words. This picture is intended for a friend of mine (a doubting Thomas), who did’nt believe my latest work on enabling a multi-factor authentication based “Web SSO” that uses on-card credentials (PIN + PKI + Biometrics) using PIV card. This solution is currently tested to run Sun OpenSSO Enterprise 8 (running on Glassfish v2), ActivClient (from ActivIdentity) and BioSP (from Aware) and PIV Smartcards on a Sun Ray environment. It works. If you are curious to know this special sauce, please bear with me. I will post the documentation including solution ingredients and other configuration details …very soon.
A picture is worth a thousand words. This picture is intended for a friend of mine (a doubting Thomas), who did’nt believe my latest work on enabling a multi-factor authentication based “Web SSO” that uses on-card credentials (PIN + PKI + Biometrics) using PIV card. This solution is currently tested to run Sun OpenSSO Enterprise 8 (running on Glassfish v2), ActivClient (from ActivIdentity) and BioSP (from Aware) and PIV Smartcards on a Sun Ray environment. It works. If you are curious to know this special sauce, please bear with me. I will post the documentation including solution ingredients and other configuration details …very soon.
Biometric Smartcards for Fishermen Identification @India
Biometric smartcards are made compulsory for sea-going fishermen from January 1, 2009, who reside in the Mangalore coast of Karnataka (India). It is very surprising to note this initiative from a local government organization steps up to enhance security and enforcing stronger access control – very pro-active move !
Here is the Story – Biometric attendance system at New Mangalore port
 It would be interesting to see how the biometric system addresses “False Rejection Rate (FRR)” cases among fishermen (due to quality of fingerprints) and how it handles the enrollment and authentication processes – when the quality of fingerprints from fishermen is degraded as it is usually/highly susceptible to Wet fingers, Skin abrasion, Skin disease, Minutia Scarcity and related problems. Usually the security gurus feel, FRR should’nt be a big issue till it blows up high and raised to become an user-experience issue (When an influential guy is blocked out)!!
It would be interesting to see how the biometric system addresses “False Rejection Rate (FRR)” cases among fishermen (due to quality of fingerprints) and how it handles the enrollment and authentication processes – when the quality of fingerprints from fishermen is degraded as it is usually/highly susceptible to Wet fingers, Skin abrasion, Skin disease, Minutia Scarcity and related problems. Usually the security gurus feel, FRR should’nt be a big issue till it blows up high and raised to become an user-experience issue (When an influential guy is blocked out)!!
As long as the organization fail to grasp on the nuts and bolts of biometric systems, the potential dangers still remain.
Terror attacks in Mumbai – Barbarism in the name of religion
Today is thanksgiving day here in the USA – I am deeply and sorrowfully affected by the time of crisis in my Indian motherland – due to menace of terrorism  and cowardice acts practiced in the name of religion. Last night, heavily armed gunmen stormed into hotels, tourist attractions and train stations and carried out attacks on innocent civilians killing 100+ and injuring 300+ people. Mumbai experienced bomb blasts before… and now more and more again – as I read from News media the ordeal is not over yet. Those heart-less terrorists are still keeping hostages and remain hiding in the hotels. One thing for sure, terrorism has NEVER won in the history and it NEVER will.
and cowardice acts practiced in the name of religion. Last night, heavily armed gunmen stormed into hotels, tourist attractions and train stations and carried out attacks on innocent civilians killing 100+ and injuring 300+ people. Mumbai experienced bomb blasts before… and now more and more again – as I read from News media the ordeal is not over yet. Those heart-less terrorists are still keeping hostages and remain hiding in the hotels. One thing for sure, terrorism has NEVER won in the history and it NEVER will.
Of all the places that were on the attack, I am very saddened to find my favorite places were hit. Looking into my past, I fondly remember my days when I toured with my friend Krishnamoorthy staying at Taj Mahal Hotel and had some good international food and drinks at Leopold Cafe. During my college days, I also experienced the fun of touring/shopping around Victoria terminus (Chatrapati Shivaji Terminus).
My condolences go to all the people affected by these acts of terrorism. We are all world citizens – It is time for decisive global action against these brain-dead fundamentalists.
Apple addict ?
Our blog is back ….in action !
Finally, I had some time to play with WordPress 2.6.5…and did have success with importing those old stuff to new Sun MySQL database and the themes/customizations (the PHP scripts were too old so i ended up doing wild guess then hack)….to make it run on WordPress 2.6.5 – it works ! Editing those messed up PHPs was an interesting experience. Still I have so much old stuff…am trying my best to migrate in to this new site soon. If it did’nt work, I will blame it on those RSS or whatever standards that supposed to take care of these issues.
Last ditch efforts did’nt help…sorry to note all the comments you folks posted were lost !!
The good news is I am dumping my blogger.com account.
Stinking Rich-clients: How to secure them ?
Yes, the demand for rich clients and rich-client-like Web applications are definitely overwhelming for its look and feel performance. When we think of rich clients over Web, we often think of applets as a solution in  the first place and we forget to consider other promising options like Java Web Start (JWS) and other Web 2.0 interfaces via Ajax and Java Server Faces (JSF). Having said that, I would like to explore your specific concerns related to applet sandbox vulnerabilities!
the first place and we forget to consider other promising options like Java Web Start (JWS) and other Web 2.0 interfaces via Ajax and Java Server Faces (JSF). Having said that, I would like to explore your specific concerns related to applet sandbox vulnerabilities!
In most cases I found the common compromises are due to browser-specific vulnerabilities and missing access control policies to its SecurityManager for restricted execution and access to its local file system. Enforcing stringent access control policies (using a policy file) and usage of signed applets are often considered to be best practice options for deploying secure applets. The Java 2 platform introduced the notion of signed applets, which allows signing an applet to ensure an applet’s origin and its integrity are guaranteed by a certificate authority (CA). The signed applet can be trusted to run with the permissions granted in the policy file defining the access control privileges for its execution and local resources. More importantly, it is important to verify your target client browser for any known security vulnerabilities related to Java applet plug-in and its runtime environment.
Although applets are very compelling in a Web environment, I would suggest considering JWS and JSF as two alternative solutions to building applets. JWS is a full-fledged application that allows Java rich-client applications to be deployed, launched and updated from a Web server. The underlying technology of JWS is Java Network Launch Protocol (JNLP), which provides a standard way for packaging and provisioning the Java application (as JAR files) and then launching them over a network. From a security perspective, JWS applications run outside a Web browser using the sandbox features of the local Java Runtime Environment (JRE). JWS also allows defining security attributes using a JNLP descriptor for client-side Java applications and their access to local resources such as file system access, making network connections and so on. JWS also support the use of signing JAR files (similar to applets) in order to verify the application origin and its integrity so that it can be trusted before it is downloaded and executed on the local machine.
JSF is another promising Web client presentation solution runs using a server-side J2EE environment similar to Java Server Pages (JSPs) and servlets, augmented with the power of rich-client like UI components. With JSF, developers can add Asynchronous JavaScript and XML (Ajax) functionality by inserting specialized AJAX/JavaScript technology code. JSF adopts the J2EE Web container security mechanisms to enforce security and controlled access to operations and their underlying resources. The Web container security features include authentication, authorization, secure session handling, transport-layer security, single-sign on access and so forth. For implementation specific details, I would suggest referring to Core Java Server Faces in conjunctiion with Core Security Patterns for supporting design patterns and best practices.
Enabling Smart Card based PKI as Java Key Store
Last week, I was test driving a PIV Smartcard based PKI as a keystore (via Java PKCS#11) to support using the PKI/certificate credentials for performing encryption/decryption and digital signature operations (PKI based logins to Web applications, Encryption/decryption of documents, Digitally signing email). There is no secret receipe but some of you may find it a bit difficult – if you are doing it for first time. So, here is my quick cheat sheet for your better understanding :
Since J2SE 5.0, JCE introduced support for the PKCS#11 standard that allows the following:
- Using hardware cryptographic accelerators for enhancing performance of cryptographic operations.
- Using smart cards as key stores for key and trust management.
To use these services, it is necessary to install the PKCS#11 implementation provided by the hardware accelerator and smart card vendors. As part of the J2SE 5.0 bundle (and up), Sun facilitates a SunPKCS#11 provider.
To use a smart card as a keystore or trust store, set the javax.net.ssl.keyStoreType and javax.net.ssl.trustStoreType of the Java runtime system properties to “pkcs11“, and set the javax.net.ssl.keyStore and javax.net.ssl.trustStore system properties to NONE. To specify the use of a vendor smart-card provider, use the javax.net.ssl.keyStoreProvider and javax.net.ssl.trustStoreProvider
Java runtime system properties to identify them. (For example: “SunPKCS11-smart card”). By setting these properties, you can configure an application to use a smart-card keystore with no changes to the application that previously accessed a file-based keystore.
Configuring a Smart card as a Java Keystore (using OpenSC Framework)
![]() The following example shows how to configure OpenSC supported smart card as a Java keystore and list the certificates using the keytool utility. The OpenSC framework can be downloaded from http://www.opensc.org.
The following example shows how to configure OpenSC supported smart card as a Java keystore and list the certificates using the keytool utility. The OpenSC framework can be downloaded from http://www.opensc.org.
- Add the OpenSC PKCS#11 module as the keystore provider in java.security file located at $JAVA_HOME/jre/lib/security/java.security.
security.provider.1=sun.security.pkcs11.SunPKCS11 /opt/openSC/openscpkcs11-solaris.cfg
- Create the OpenSC PKCS#11 configuration file. For example, the openscpkcs11-solaris.cfg looks like as follows:
name = OpenSC-PKCS11
description = SunPKCS11 w/ OpenSC Smart card Framework
library = /usr/lib/pkcs11/opensc-pkcs11.so - With the above settings, it is possible to use the smart card as a keystore and retrieve information about the certificates from your Smartcard. For example, you may use the keytool utility to list certificate entries from a smart card:
$ keytool -keystore NONE -storetype PKCS11 -providerName SunPKCS11-OpenSC -list -v
Enter keystore password: <SMARTCARD_PIN>
Keystore type: PKCS11
Keystore provider: SunPKCS11-OpenSC
Your keystore contains 4 entries
Alias name: Signature
Entry type: keyEntry
Certificate chain length: 1
Certificate[1]:
Owner: SERIALNUMBER=79797900036, GIVENNAME=Nagappan Expire1779,
SURNAME=R, CN=Nagappan (Signature), C=US
Issuer: CN=Nagappan OpenSSL CA, C=US
Serial number: 1000000000102fdf39941
Valid from: Sat Nov 01 15:29:22 EST 2008 until: Wed Jun 01 15:29:22 EST 2009
Certificate fingerprints:
MD5: 12:20:AC:2F:F2:F5:5E:91:0A:53:7A:4B:8A:F7:39:4F
SHA1:
77:76:48:DA:EC:5E:9C:26:A2:63:A9:EC:A0:14:42:BF:90:53:0F:BC
Alias name: Root
Entry type: trustedCertEntry
Owner: CN=Nagappan OpenSSL Root CA, C=US
Issuer: CN=Nagappan OpenSSL Root CA, C=US
Serial number: 11111111111111111111111111111112
Valid from: Sat Nov 01 15:29:22 EST 2008 until: Wed Jun 01 15:29:22 EST 2009
Certificate fingerprints:
MD5: 5A:0F:FD:DB:4F:FC:37:D4:CD:95:17:D5:04:01:6E:73
SHA1:
6A:5F:FD:25:7E:85:DC:60:81:82:8D:D1:69:AA:30:4E:7E:37:DD:3B
Alias name: Authentication
Entry type: keyEntry
Certificate chain length: 1
Certificate[1]:
Owner: SERIALNUMBER=79797900036, GIVENNAME=Nagappan Expire1779,
SURNAME=R, CN=NAGAPPAN, C=US
Issuer: CN=Nagappan OpenSSL CA, C=US
Serial number: 1000000000102fd10d2d9
Valid from: Sat Nov 01 15:29:22 EST 2008 until: Wed Jun 01 15:29:22 EST 2009
Certificate fingerprints:
MD5: 29:7E:8A:5C:91:34:9B:05:52:21:4E:49:5B:45:F8:C4
SHA1:
15:B7:EA:27:E1:0E:9D:94:4E:7B:3B:79:00:48:A2:31:7E:9D:72:1A
—————–
Using Sun Ray DTU as your Smart card Reader
In our case, the customer chose to use Sun Ray as the Smartcard reader where the inserted card is used for performing session mobility and PKI/Certificate based cryptographic operations. To enable access to Smartcard based PKI credentials on Sun Rays, make sure you install the Sun Ray PC/SC Lite to support accessing smart cards. You may download the PC/SC Lite for Sun Ray Server (SRSS 4.x) from:
http://www.sun.com/download/products.xml?id=46af59b2
Enjoy
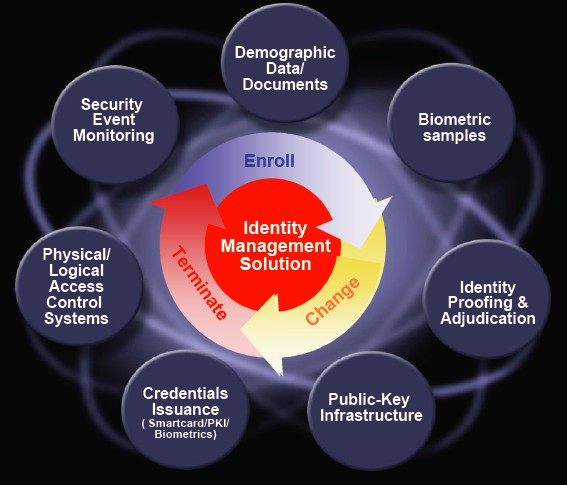
Managing PIV Lifecycle and Converging Physical & Logical Access Control
 Last week, I was at the 7th Annual Smart Card in Government Conference and had the opportunity to join a panel on “Personal Identity Verification (PIV) – Technologies” and presented a session entitled “Managing PIV Lifecycle and Converging Physical and Logical Access Control” with emphasis on implementing HSPD-12/FIPS-201 mandates. I thoroughly enjoyed my participation in the conference, particularly the overwhelming Smartcard and Biometric interests from US Federal Govt organization, Law enforcement, Defence agencies and from other countries as well.
Last week, I was at the 7th Annual Smart Card in Government Conference and had the opportunity to join a panel on “Personal Identity Verification (PIV) – Technologies” and presented a session entitled “Managing PIV Lifecycle and Converging Physical and Logical Access Control” with emphasis on implementing HSPD-12/FIPS-201 mandates. I thoroughly enjoyed my participation in the conference, particularly the overwhelming Smartcard and Biometric interests from US Federal Govt organization, Law enforcement, Defence agencies and from other countries as well.
It is quite compelling to note, the conference gave a big boost to FIPS-201 specfications that has become
the de-facto standard for Identity credentialing for Govt. Employee ID, First Responder Credentials, Airport/Transportation worker credentials, Electronic Passports (ePassports) and also sets the standards for acquiring and incorporating Demographic data, PKI/certificates and Biometrics for enabling Physical and Logical access control.
During my presence, I had quite a lot of conversations with participants for Govt agencies, SIs and ISVs about implementing FIPS-201/PIV solution and how to automate identity credentialing and pre/post issuance processes and provisioning/de-provisiong credentails to Physical access control systems and Logical access control systems (SSO/Federation) and finally how to respond to managing and auditing those discrete processes.
If you are curious to have my presentation slides, you may grab it here : Managing PIV Lifecycle and Converging Physical and Logical Access Control.
Enjoy.