A secure data protection using encryption depends more on secure key management processes than the encryption itself. Although enabling encryption looks quite trivial, managing the underlying Key management lifecycle processes and handling the associated cryptographic operations always been a daunting challenge! The challenges are too many till we really know..beginning from key generation and issuance, key ownership, key usage, privileged users of keys, key access controls, least privileges, separation of duties, key rotation, key distribution, key expiry and destroyal and much more, depending on the risk profile you deal with! So don’t get fooled by how easy is encryption. If everything worked out well as expected in the first place, just be happy! When things go wrong…be prepared for the worst happens..yes, you may lose the keys or lose access to encrypted data forever. How much are those keys well protected and securely persisted in the storage? the question leads to the Key store stakeholders, security of Key Encrypting Keys (KMK) and the Master Key of the key store itself. On the other side, you may find the abuses of a single key for everything, not just data encryption… from authentication, key encryption, digital signatures and so on. Believe it or not, many of us will realize the actual risks of key management and its potential consequences till we really encounter the problems associated with sensitivity of data exposure in terms of its confidentiality, integrity, privacy or compliance breach. Mismanagement and poor choice of encryption algorithms and related key management practices can ultimately compromise resulting encryption make no sense at all. When we encounter such problems, the afterthought options for post-mortem solutions are usually very limited. Adopting to Hardware Security Modules (HSM) has always been helpful to address several known risks of key management lifecycle processes and securely handling cryptographic operations. That said, I shouldn’t forget to mention HSMs adds significant costs for encryption.
For the past 6 months also, I had been reviewing and testing encryption and key management options in AWS and it has been a pleasant adventure of understanding who owns the risks and controls. Managing encryption and key management in the AWS Cloud looks like a piece of cake till we understand the different options and its risk profiles. AWS Key Management Service (KMS) and AWS CloudHSM are the two options available for handling key management lifecycle process and supporting cryptographic operations.
KMS is an AWS managed service for Cloud consumers that allows handling select key management lifecycle processes and facilitates symmetric key operations for encrypting data particularly encrypting AWS Block Volumes (EBS), Simple Storage Service (S3) Buckets, encrypting Redshift Data warehouses, Databases residing in Relational Database Service (RDS), Data stores in Elastic MapReduce (EMR). AWS KMS facilitates a Two-tiered envelope encryption operational model using Master Key (Customer Managed Key or AWS Managed Key – Default Key) and Data Keys. Master Keys encrypt data keys used for encryption. Master keys supposedly do not leave AWS KMS service (evidently AWS owned HSM). AWS relies on IAM services to define and assign policies for users and roles to create, manage, use and delete keys. As KMS is a managed service, it manages the rotation of keys and assures highly available key storage available for management via AWS IAM service and Key auditing through AWS CloudTrail services. KMS also provides Bring-Your-Own-Key (BYOK) option where customers can import AES-256-XTS keys in PKCS#1 standard format.
Alternatively, CloudHSM is a customer-owned and managed Hardware Security Module (HSM) that allows using a dedicated single tenant HSM for a Cloud customer. AWS owns the responsibility of provisioning the HSM in customer’s VPC environment in AWS. While the use of HSM certainly allows a customer to have full control over the keys residing in the HSM, its key management lifecycle processes, cryptographic operations and even accelerating them for performance.
For a better comparison of AWS KMS and AWS CloudHSM, here is my review of both services in terms of security controls and features (I added pricing too ~Early 2018)
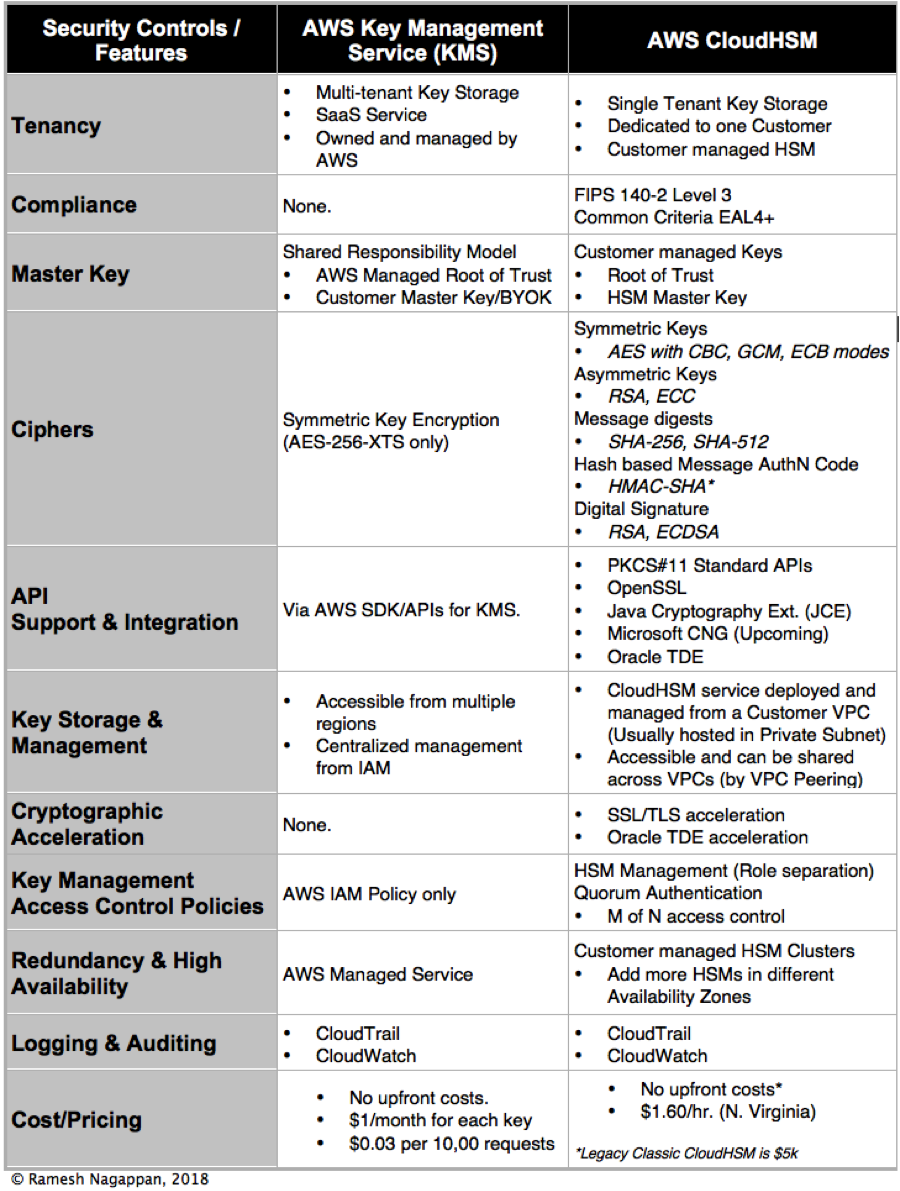
Comparative Study – AWS Key Management Service (KMS) vs. AWS CloudHSM
Many years ago… during my good old days of Sun Microsystems, I was attending a casual meeting with Dr.Whitfield Diffie (Co-Father of Public Key Cryptography) he said: “An amateur hacker attacks the encryption to hack the resource whereas the experienced hacker just looks for the ways to get access to the key itself”.
So save the keys carefully and manage them wisely 🙂
References:
AWS Key Management Service Whitepaper
Excellent deep dive comparison of KMS with CloudHSM!
Great breakdown, thanks!
Amazing article, it clarified many of my doubts/confusions around AWS offered Key management solutions. Thank you!
You should consider updating your content. Lots of old facts here. Both KMS and CloudHSM have evolved.