 Java Card technology has been a passion of mine for so long and I always tried my best to keep updated on Smart card technologies…… not just because of my role at Sun, I did get several opportunities to work closely with citizen-scale Java Card deployments with multiple National ID, eID/ICAO, US DoD/CAC, PIV/FIPS-201 cards and related Identity management projects. It is always been quite adventurous everytime to experience a card issuance architecture and deployment scenario – right from applicant enrollment, demographic data provisioning, Biometrics/PKI credentialing, adjudication/background checks, post-issuance maintenance including card authentication/verification/usage and final retirement/termination. In the early 2000’s, I even had an opportunity to write couple of Java Card applets for a big 5 financial organization using Java Card 2.x and it is still exists on production (No kidding! one of them may be in your wallet). With all those experiences, I did have my own stumbling issues with programming Smartcards, where I pulled my hair-out on understanding those evil “Application Protocol Data Units” (APDU) based commands and responses. In my opinion, APDUs are quite complex to understand when you jump in unless you read the docs in-and-out beforehand and then test-driving APDUs are even more hard unless you have the luxury of having a debugging environment – seriously, you may not want to experience those pains. Havingsaid, now we can breathe a sigh of relief – I am bit late to experience the newer features of Java Card 3.0 – It has introduced “network-centric” and “Java/J2EE developer” friendly features that radically changed the way we originally designed, developed, deployed, and integrated Smartcard applications. Interestingly, there are very compelling aspects about Java Card 3.0 technology – As I digged with my little experience… here is my observations.
Java Card technology has been a passion of mine for so long and I always tried my best to keep updated on Smart card technologies…… not just because of my role at Sun, I did get several opportunities to work closely with citizen-scale Java Card deployments with multiple National ID, eID/ICAO, US DoD/CAC, PIV/FIPS-201 cards and related Identity management projects. It is always been quite adventurous everytime to experience a card issuance architecture and deployment scenario – right from applicant enrollment, demographic data provisioning, Biometrics/PKI credentialing, adjudication/background checks, post-issuance maintenance including card authentication/verification/usage and final retirement/termination. In the early 2000’s, I even had an opportunity to write couple of Java Card applets for a big 5 financial organization using Java Card 2.x and it is still exists on production (No kidding! one of them may be in your wallet). With all those experiences, I did have my own stumbling issues with programming Smartcards, where I pulled my hair-out on understanding those evil “Application Protocol Data Units” (APDU) based commands and responses. In my opinion, APDUs are quite complex to understand when you jump in unless you read the docs in-and-out beforehand and then test-driving APDUs are even more hard unless you have the luxury of having a debugging environment – seriously, you may not want to experience those pains. Havingsaid, now we can breathe a sigh of relief – I am bit late to experience the newer features of Java Card 3.0 – It has introduced “network-centric” and “Java/J2EE developer” friendly features that radically changed the way we originally designed, developed, deployed, and integrated Smartcard applications. Interestingly, there are very compelling aspects about Java Card 3.0 technology – As I digged with my little experience… here is my observations.
Understanding Java Card 3.0
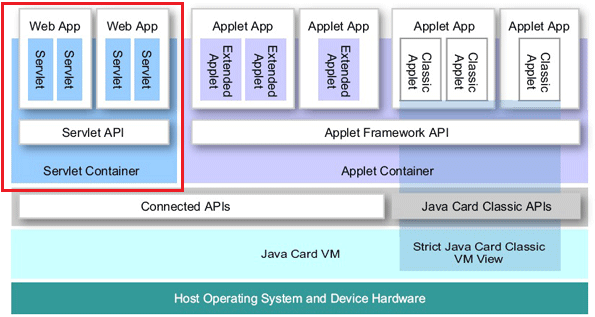
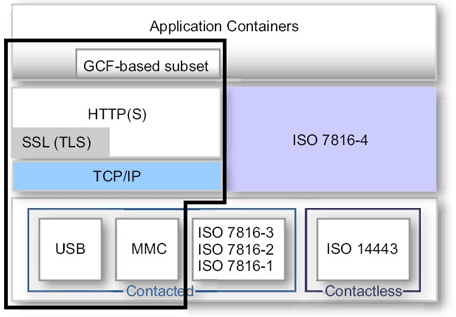
- A Smartcard can act as a “Personal Web Application Server” or an user-centric miniature Java EE application server on a network. Java Card 3.0 has introduced a Servlet container environment referred to as “Connected Edition” – which allows the smartcard applications can built as Java servlets (Web applications) using Servlet 2.4 APIs and deployed as a “WAR” file to the Web container running on a Java Card 3.0 compliant Smart card. This Servlet based deployment is an addition to existing Java card applet deployment model referred to as Classic Edition (exists with Java card 2.2.x). The Java Card clients access the applications using a Web browser (ex. http://localhost:8019/myJavaCardServlet).
- Java Card 3.0 supports 32-bit processor based Smartcards and handles more memory – upto 128k.
- Enough with pain of understanding/testing APDUs, now you can readily develop Java Servlet 2.4 API compliant Web applications and deploy them to a Smart card.
- With Java Card 3.0, we can perform interact with using standards based communication with the card using HTTP/HTTPS and also its supporting XML based protocols such as SOAP, REST etc.
- Support for Java crypto APIs and additionally you can enable access control with the card similiar to performing container-managed authentication in Java EE – using SSL/TLS mechanisms.
- Java Card 3.0 based Web applications can be developed, debugged and deployed using Netbeans 6.7.1 and up.
- Smart card issuance (for Card holders) and updates using GCF can be done through Web based deployment model (via HTTP, TCP) – using both contact and contactless communication interfaces.
- Other features include full Java language support (Java 1.6 features) including all data types (except float and double), multi-threading, garbage collection, XML parsing/generation capabilities etc.
- Allows Java developers to explore Java Card platform easily with strong potential for deploying security applications intended for National ID card schemes, passports and simplifying deployment of “Match-to-card Biometrics”, “On-card” credential persistence and secure transaction based applications.
Try it yourself
If you are curious to test drive Java Card 3.0 reference implementation especially using its “Connected Edition” to deploy Java Servlet based application to Smart card – Before you begin, make sure you obtain the list of pre-requistes :
and then proceed with the following steps for deploying a “Hello World” Web application – creating Java card applications can’t get easier than this :
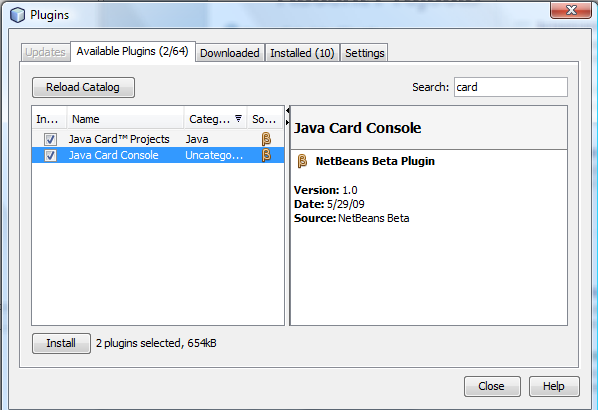
- Install the Java Card 3.0 plugins for Netbeans 6.7.1 – Go to Tools, Plugins and search for card to select plugins for “Java Card Projects” and “Java Card Console”.
-
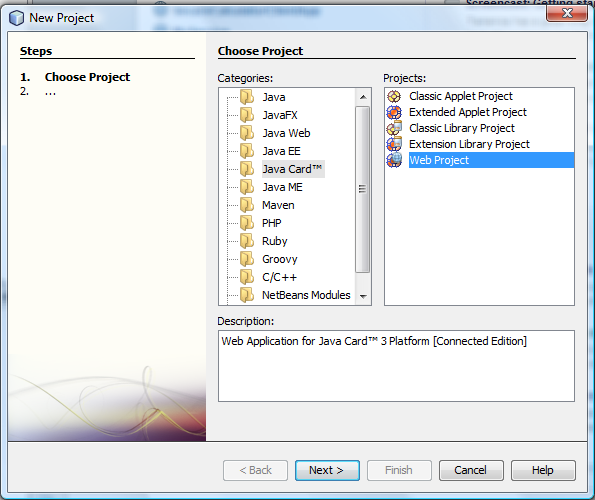
Go to Netbeans IDE, Choose Project – “Java Card” and select Projects type “Web Project”.
-
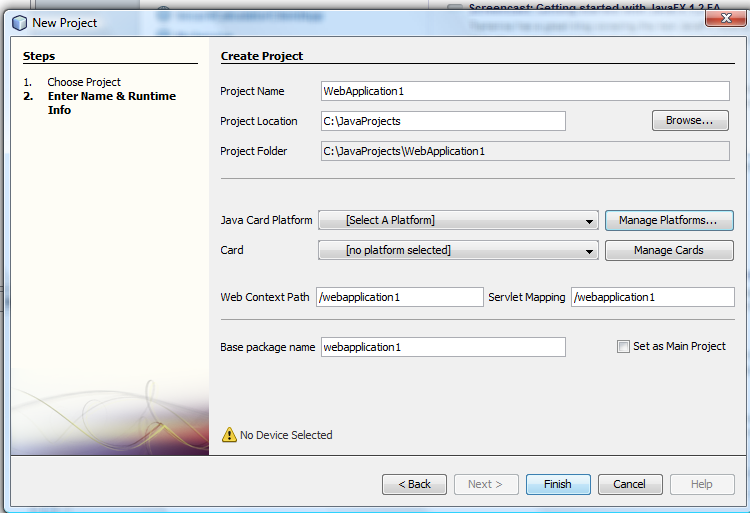
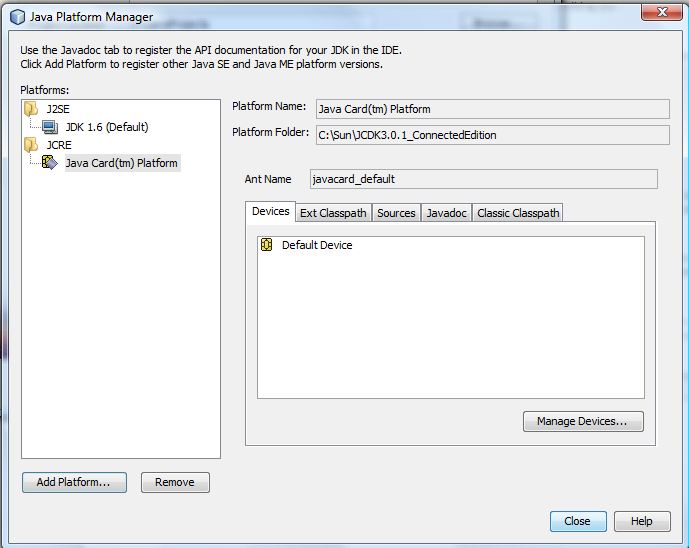
Assign Project name/location/folder and then select “Manage Platforms” to assign the Java Card 3.0 runtime environment.
-
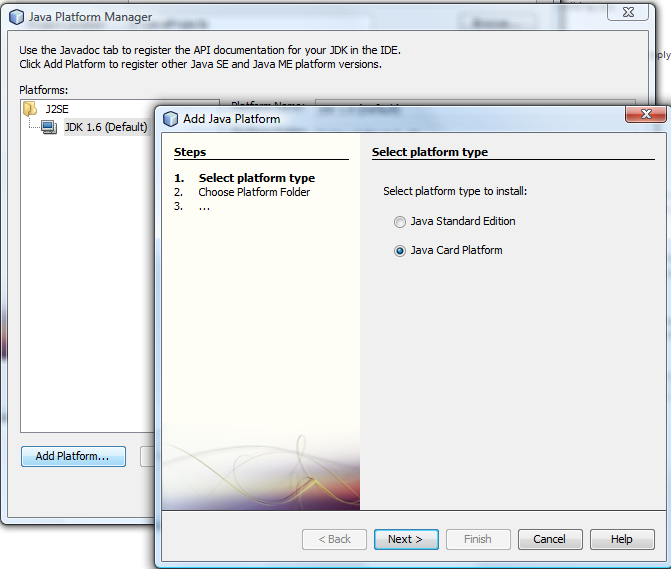
To assign the Java Card runtime info, select “Manage Platforms” and choose “Platform type” to Java Card Platform.
-
Select the location of your “Java Card 3.0 Connected Edition Dev kit” installation.
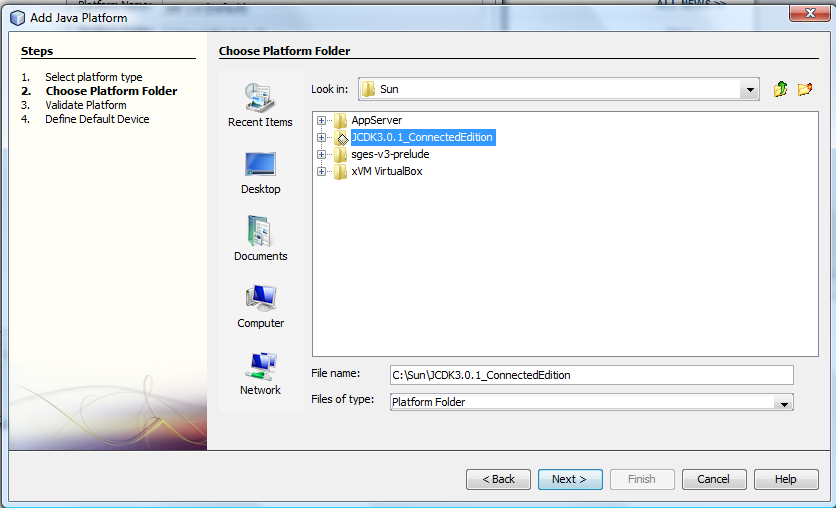
-
Define the default device (assuming your Smartcard) attributes and press “Finish”:
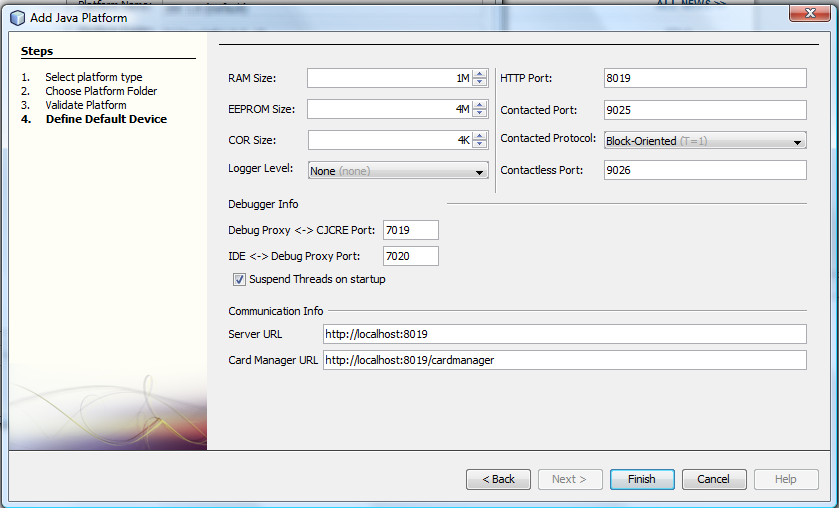
-
To deploy and run the Web application from your target Smartcard device (in my case the JavaCard RI), In the Projects window, right-click the project node and choose Load/Create Instance or just Run to run the application. Netbeans will launch the browser, displaying the Hello world application prompting for your name…. and push the button to see – what happens !
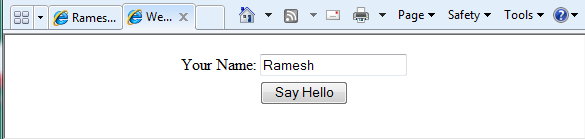
Netbeans does all the magic for you – if something not working, no worries ! Like implementing anyother Web application in IDE, it is now easy for you to painlessly debug and redeploy the application – I am sure, you’ll find deploying applications on Java Card is nolonger a mystery.
With Billions+ Java Cards already in use and so much demand for the Smartcard technology, Java Card 3.0 promises beyond citizen IDs and can potentially act as your “Personal Web application server” on your wallet.
Thanks to Anki Nelaturu and Saqib Ahmad who introduced me to Java Card 3 with their JavaOne ’09 sessions. After playing with my first excercise on Java Card 3.0 RI, now I am chasing my friendly Smartcard vendors to loan me couple of Java Card 3.0 cards 🙂




 University of Johannesburg (South Africa), explains how a person’s biometric fingerprints/Iris scans can be used as a protocol to perform private key based encryption and digital signatures. The paper describes a biometric middleware infrastructure (BioVault) which requires users to performs biometric authentication for generating or retrieving a random key from user’s keystore. The selected key is used to perform the required encryption or signature operation. If Alice and Bob exchanges messages using their secret key they are required to authenticate with biometrics. The only advantage of this process is the user don’t need to remember a password or carry a smartcard/PIN to support accessing their keystore – as it uses fingerprint or Iris pattern based authentication prior to initiating the operations.
University of Johannesburg (South Africa), explains how a person’s biometric fingerprints/Iris scans can be used as a protocol to perform private key based encryption and digital signatures. The paper describes a biometric middleware infrastructure (BioVault) which requires users to performs biometric authentication for generating or retrieving a random key from user’s keystore. The selected key is used to perform the required encryption or signature operation. If Alice and Bob exchanges messages using their secret key they are required to authenticate with biometrics. The only advantage of this process is the user don’t need to remember a password or carry a smartcard/PIN to support accessing their keystore – as it uses fingerprint or Iris pattern based authentication prior to initiating the operations.


