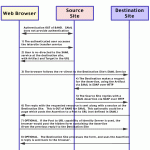
Last week, I was at Biometric Consortium Conference 2006 to present “Biometric Single Sign-On using SAML: Architecture and Design Strategies” and demonstrate one of my favorite topic of interest – Stronger authentication solution that combines “Web Access Management/SSO/Federation” using “Biometrics”. I used my previous JAAS Module integration work between Sun Java System Access Manager 6.x (SunONE Identity Server) and BioBex (Advance Biometric Controls) and then extended it to configure SAML Browser Artifact Profile, that enables SAML based SSO between an IdP (Sun Access Manager) and a J2EE application.
For those curious, here is the link to my presentation….”Biometric Single Sign-On using SAML: Architecture and Design Strategies“.
Enjoy !