In a Blockchain infrastructure, trust is built using cryptographic hash functions and Public-key cryptography using digital signature mechanisms. If we unpack the building blocks of a typical blockchain infrastructure – It relies on a multi-party peer-to-peer transactional network backbone without relying on a central authority. On the blockchain network, the peers create transactions, collaborate on transactions, validate and verify the transaction for correctness and may choose to endorse or reject them using a consensus protocol. Each peer node on the network collects those series of transactions, once endorsed and committed by their peers they are grouped and stored as blocks in a single system of record keeping called Ledger. The copies of the blocks are distributed to the peers by replication and then the blocks are synchronized into each of their ledgers. To ensure “Proof-of-Work” and assuring the authenticity and data integrity of the ledgers in all peers with indelible record keeping, non-repudiation, and tamper-proof immutability, the stack of transactions are validated and endorsed by a multi-party consensus protocol that applies one-way hash functions and digital signatures in each block before it is stored in the distributed ledger. As a result, every committed blockchain transaction results including valid cryptographic material in the block.
Relevance of Hash and Signatures in Blockchain
Before we delve into blockchain representation of hash and digital signatures, for those who needed some background on the usage and the relevance:
- Creating a Hash is a mathematical/cryptographic function which takes an input message (alphanumeric string) and converts it to a fixed-length alphanumeric string. As each hash produced for a message is unique, it acts like a signature for the provided message and the hashing process is irreversible. With hashes, the blockchain creates a linked list of data and a hash pointers which point to its previous block and its next block, hence it results in creating the blockchain. Use of hashes in the blockchain helps to demonstrate “Proof-of-Work”, assures maintaining data integrity and keeping the ledger tamper-resistant. In Blockchain, the cryptographic hash algorithms for creating hashes are SHA-256 and RIPMD-160.
- Creating digital signature is a mathematical/cryptographic function based on public-key cryptographic mechanisms. Using public-key crypto algorithm, we can generate a Public/Private key pair both are mathematically linked. The private key will be kept secret by the owner and the public key can be distributed publicly. To create a digital signature, the owner/signer creates a one-way hash of the message (alphanumeric string) to be signed. Then the owner uses the private key to encrypt the hash. The encrypted hash is referred to as a digital signature. Creating a hash to fixed length value and encrypting the hash makes a smaller size which is easier to verify. To verify the digital signature, the receiver uses the public key to decrypt the hash and recomputes the hash for the message and checks to match the value of the hash sent to verify if the document is modified. In blockchain infrastructure, a Wallet software program is used to generate the public/private key pair and store the private key of the owner. Each blockchain node owner owns Public/Private key pair, where the public key is used to create the hash addresses and the corresponding private key is used for signing (encrypting the hash). The verification of the signature using the public key can be done by decrypting the hash and verify the hash value. In a Blockchain, the public-key cryptographic algorithm used for creating the digital signature is Elliptic Curve Digital Signature Algorithm (ECDSA).
How is it being used in BitCoin?
In the bitcoin world, typically a bitcoin address is a 160-bit hash of the public key portion of a public/private key pair of a node owner. The bitcoin address represents a destination of a payment. “Pay to Public Key Hash (P2PKH)” is the standard format for representing Bitcoin address, it refers to Pay to a hash of a public key (P2PKH)of the owner – P2PKH addresses start with “1”. Bitcoin also supports another format which refers to P2SH (Pay to Script Hash) address – which starts with 3. In a typical bitcoin user scenario, the bitcoin wallet collects entropy (random numbers) and then uses it to create an ECDSA private key and then derives a public key related to the private key. Using public key (as P2PKH) the owner can send and collect bitcoin payments. To create a bitcoin address, the wallet hashes the public key with SHA 256 and the result with RIPEMD-160. The waller adds the bytes 00 as a prefix which is called the version byte (as a result P2PKH addresses starts with a base58 prefix 1) and four checksum-bytes (as error checking code) added at the end of the resulting hash string. In case of P2SH address, the sender pays to the hash of a script. In case of P2SH, the wallet uses the prefix 05 (as a result P2SH addresses starts with a base58 prefix “3”). Thus the Private Key is used to generate a signature for each blockchain transaction (cryptocurrency) the owner sends out, which confirms that the transaction is initiated by the owner’s private key and it cannot be tampered by anyone. To receive a blockchain transaction (cryptocurrency) from a sender, the sender uses the hash of the owner’s public key which corresponds to the owner’s private key.
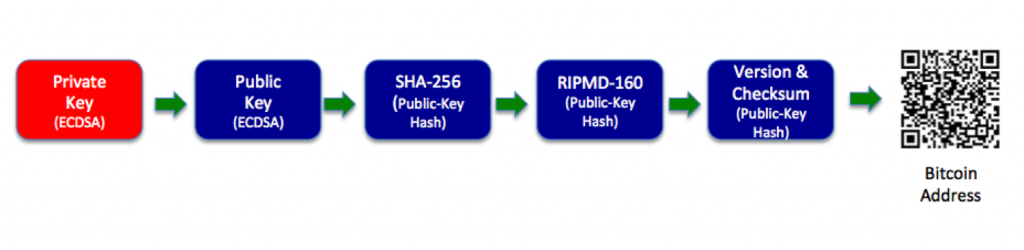
Creating a Blockchain address using Hash and Digital Signature (ex. Bitcoin Address)
Starting with the public key K, we created the SHA256 hash and then created the RIPEMD160 hash. As a result, it will produce a 160-bit (20-byte) number., where K is the public key and BA is the bitcoin address.
Bitcoin address BA = RIPEMD160(SHA256(K))
In addition, we will add the Version Prefix and Checksum. The resulting Bitcoin address is delivered to the users in “Base58Check” encoding.
An example P2PKH address would look like this:
1J43KLMCxcochXpLhjM7g3MxMMTHPj3zLXc
How about Ethereum?
Like Bitcoin, Ethereum also uses ECDSA algorithm for creating digital signature but for creating hashes Ethereum uses Keccak-256 as its hashing algorithm. Both Bitcoin and Ethereum use Cryptocurrency wallets programs to store public and private keys and interface with the blockchain network to enable users to send and receive cryptocurrencies.
How simple is a CryptoCurrency Wallet?
Blockchain is the most popular wallet that supports both Bitcoin and Ethereum networks.
Here is an example:
Example – BitCoin Wallet