Manually assessing security controls, host and application configuration, access control policies, software patch levels and creating on-demand compliance readiness reports has always been a daunting task, especially when it is critical to adhere standards and regulatory mandates. Not only those processes are very time consuming and they are also highly prone to human errors. It becomes even more complicated when Security professionals unfamiliar with the target resource often struggle to identify technical controls, particularly to find ways to answer the following questions:
- Does the hosted system and applications meet the organization’s security policies?
- Does the hosted system and applications are configured right and patched to the appropriate levels addressing all known vulnerabilities?
- How can we review default configuration settings, ports, protocols, and services are effective and in use?
- How can we perform individual checks for critical security controls and report the results of each of those checks performed?
- How to measure risks in terms of metrics for vulnerabilities assigning severity levels?
Answering those questions becomes, even more, harder if those processes need to be repeated for periodic reviews and to sustain compliance mandates. Thus, it is extremely critical to automate using a standards-based approach that is easily repeatable to help on-demand evaluation and reviews. This will help quickly review system configurations, installation and presence of minimum required security policies, updates, patches, system security configuration settings and all known vulnerabilities related to unnecessary ports and protocols and finally minimization of hosted applications in alignment with industry standards (such as PCI-DSS) and regulatory mandates such as HIPAA, FISMA and others.
What is SCAP?
Based on the NIST Special Publication 800-53 (SP 800-53) controls framework, the “Security Content Automation Protocol (SCAP)” is a NIST defined standard to enable automation of vulnerability management, vulnerability measurement, and security compliance assessment for systems. The scripts follow standards using “Open Vulnerability and Assessment Language” (OVAL) and Extensible Configuration Checklist Description Format (XCCDF). A typical SCAP implementation will include the following components:
- Common Vulnerabilities and Exposures (CVE) – Industry standard for Enumeration for software vulnerabilities using Common name identifiers
- Common Platform Enumerations (CPE) – A structured naming convention used to identify IT systems (hardware), platforms (operating systems), and packages (applications).
- Common Configuration Enumeration (CCE) – A stand for uniquely identifying security-relevant configuration elements for applications and operating systems.
Additionally, it also includes components for Risk measurements:
- Common Vulnerability Scoring System (CVSS) – It facilitates a standardized way to qualitatively assess and measure by capturing the characteristics of a known vulnerability and computes a numerical score specifying its level of severity (such as low, medium, high, and critical). The severity levels help to assign a score to a vulnerability and in turn, it helps security auditors to prioritize risk.
- Common Configuration Scoring System (CCSS) – It provides a NIST standard framework for measuring the severity of software security configuration issues.
Making all these components working together, Redhat has delivered “OpenSCAP” an Open-source implementation of SCAP standard, which is available for performing automated vulnerability management, measurement, and policy compliance evaluation on Linux, BSD, Solaris and several Web servers. Lately, there is an on-going effort for porting OpenSCAP on Microsoft Windows is available and final release in progress.
OpenSCAP provides a complete framework of libraries and tools to perform configuration (configuration scanner) and vulnerability scans (vulnerability scanner) of a local system by evaluating both XCCDF benchmarks and OVAL definitions, generate the appropriate results with a compliance score. If anomalies exist it will provide remediation guidance. The OpenSCAP implementation also includes pre-built assessment profiles for common configuration requirements, such as DoD STIG, PCI-DSS, CJIS, and meeting Redhat recommended security for Cloud Provider standards. The pre-built assessment profiles can be modified/tailored to create custom assessment profiles. Once the assessment scanning is complete, OpenSCAP generates an HTML formatted report enumerating the results of the tests passed and failed to highlight the severity and the final compliance score for the system.
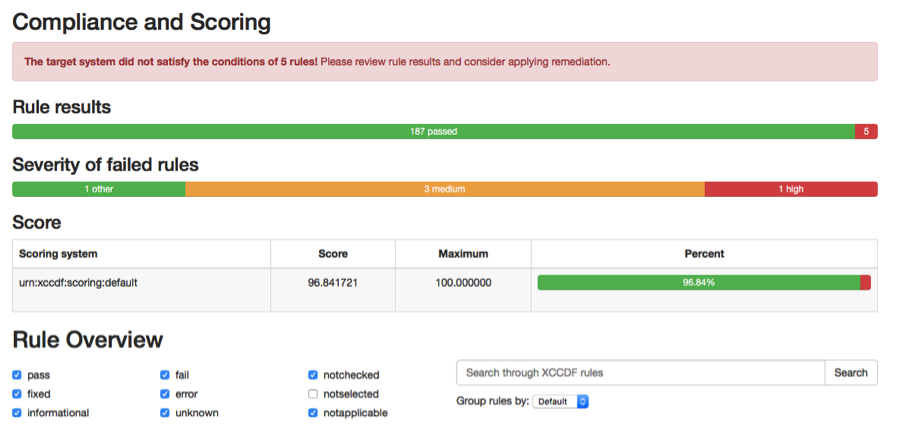
OpenSCAP Report: Compliance score report
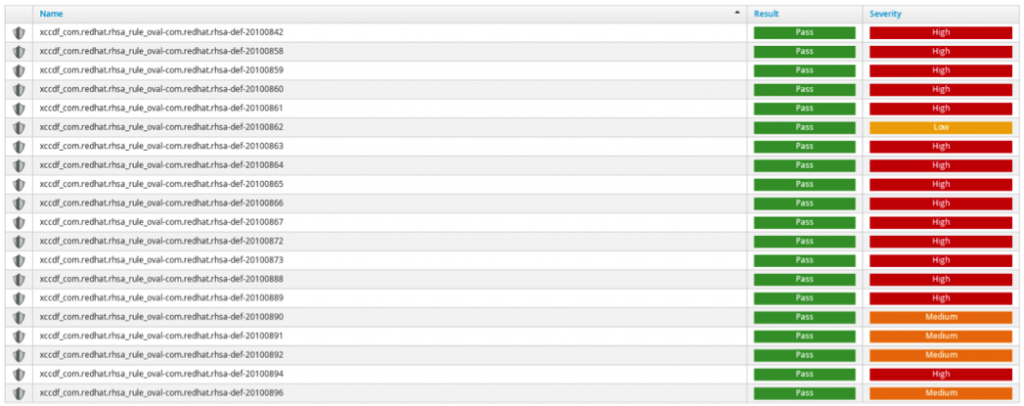
List of tests: Passed/Failed and Severity levels
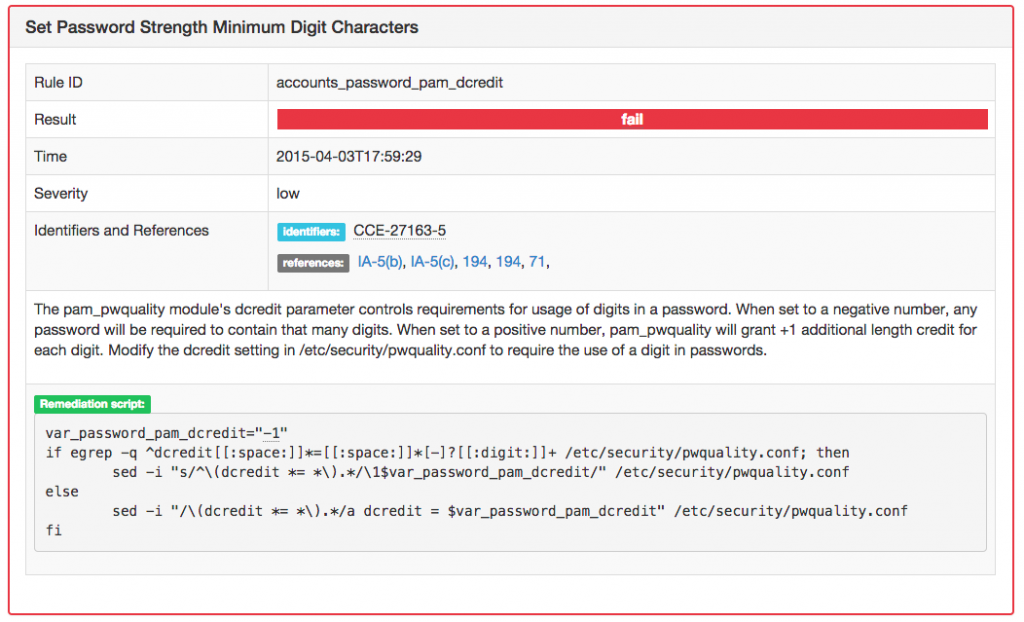
Remediation Script for Failure
How to install and use OpenSCAP ?
To install OpenSCAP on Linux OS, you are required to download and install OpenSCAP scanner and Security guide content:
# yum -y install openscap-scanner scap-security-guide
To customize and modify Security Assessment profiles to meet an Organizational policy, you may choose to tailor an existing profile to meet your needs. To download tailoring utility:
# yum -y install scap-workbench
To list of assessment profiles for use on an RHEL 7 server:
Document type: Source Data Stream Imported: 2015-10-02T06:17:44
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel7-xccdf-1.2.xml Generated: (null)
Version: 1.2
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-rhel7-xccdf-1.2.xml Status: draft
Generated: 2015-10-02
Resolved: true
Profiles:
xccdf_org.ssgproject.content_profile_standard
xccdf_org.ssgproject.content_profile_pci-dss
xccdf_org.ssgproject.content_profile_rht-ccp
xccdf_org.ssgproject.content_profile_common
xccdf_org.ssgproject.content_profile_stig-rhel7-server-upstream
Referenced check files: ssg-rhel7-oval.xml
To start an OpenSCAP assessment scan on a RHEL7 server (Run the following command in a single line):
# oscap xccdf eval –profile xccdf_org.ssgproject.content_profile_rht-ccp
–results-arf arf.xml –report report.html /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xml
Reports
The assessment process usually takes about 15 minutes on a latest Intel Xeon server, depending on the choice of assessment profile and number of rulesets included. Using SCAP Workbench will provide you a complete overview of the results and the final reports will be available in HTML for download or it can be streamed into a dashboard (like Redhat Satellite).
Further References and Resources:
SCAP Benchmarks for Operating Systems, Web Servers, and Applications
- Choose Tier-III “Should work in SCAP Validated Tool”, you should see benchmarks for Web servers, Databases, Operating Systems, and many popular software utilities.