With increasing incidents of online frauds through username/password compromises and stolen/forged identity credentials – Strong authentication using multi-factor credentials is often considered as a defensive solution for ensuring high-degree of identity assurance to accessing Web applications. Adopting multi-factor credentials based authentication has also become a most common security requirement for enabling access control to critical online banking transactions and to safeguard online customer information (Mandated by FFIEC authentication guidelines). One-time Passwords using Tokens, USB dongles, Java Smartcards/SIM cards, Mobile Phones and other specialized devices has become the most simplest and effective option that can be easily adopted as the “second-factor credential (Something I have)” for strong authentication solution. Although…and there is a myriad ways to create one-time passwords, the overwhelming developer issue is to make it to work by readily integrating it with existing applications and further enabling them for use in Web SSO and Federation scenarios.
One-time Password (OTP) Authentication using OpenSSO
The One-time password (OTP) is commonly generated on a physical device such as a token and is entered by the user at the time of authentication, once used it cannot be reused which renders it useless to anyone that may have intercepted it during the authentication process.
Sun OpenSSO Enterprise 8.x offers a ready-to-use OTP based authentication module that allows to deliver One-time passwords via SMS (on Mobile phones) and Personal email or combination of both. OpenSSO implements Hashed Message Authentication Code (HMAC) based One-time password (HOTP) algorithm as defined in RFC 4226 – an IETF – OATH (Open Authentication) joint initiative. The HOTP is based on HMAC-SHA-1 algorithm – using an increasing 8-bit counter value and a static symmetric key that is known to the HOTP generator and validation service. In a typical OpenSSO deployment, the HOTP authentication module is configured to work as part of an authentication chain that includes a first-factor authentication (ex. Username/Password authentication with LDAP, Datastore). This means that atleast one of the existing authentication must be performed successful before commencing HOTP authentication.
Try it yourself
To deploy OTP for Web SSO authentication, all you would need is to have OpenSSO Enterprise 8.x and configured up and running…. and then follow these steps:
- Login to OpenSSO Administrator console, select the “Access Control” tab, select your default “Realm”, select “Authentication”. Click on “Module Instances” and click on “New” to create a Module instance. Assign a name to the module instance (ex. HOTP) and select “HOTP” as type.
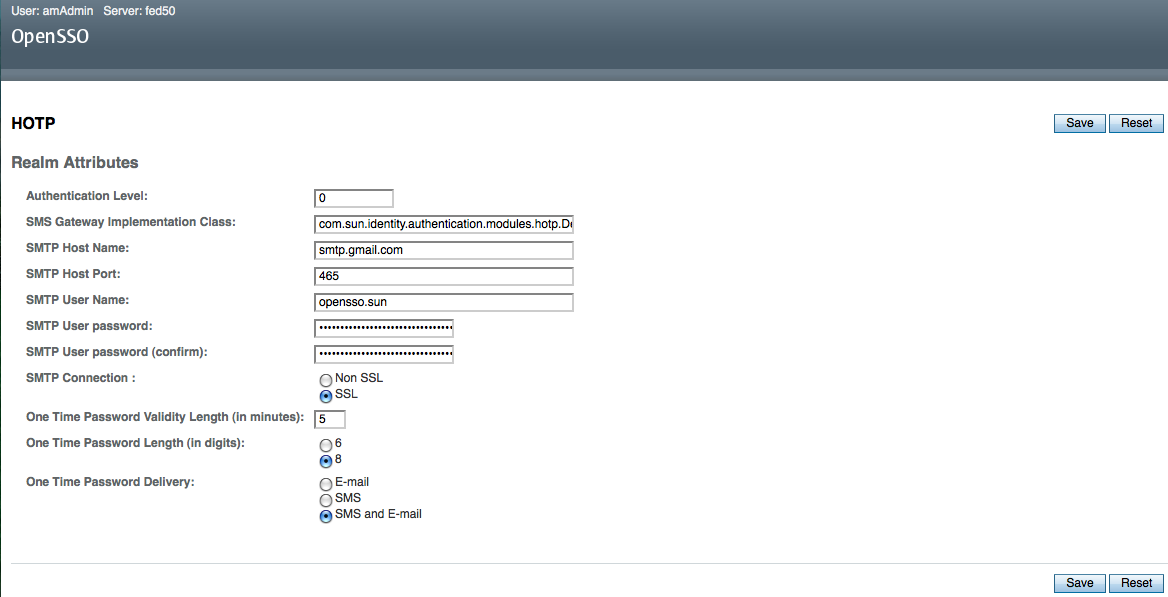
- Configure the HOTP authentication module properties. You need to identify the values for Authentication Level, SMTP Server (Access credentials including host name, port, username, password), One-time password validity length (Maximun validity time valid since creation and before OTP expires), One-time Password length (6 or 8 digits), One-time Password Delivery (“SMS” or “Email” or “Both” to receive SMS and Email).
-
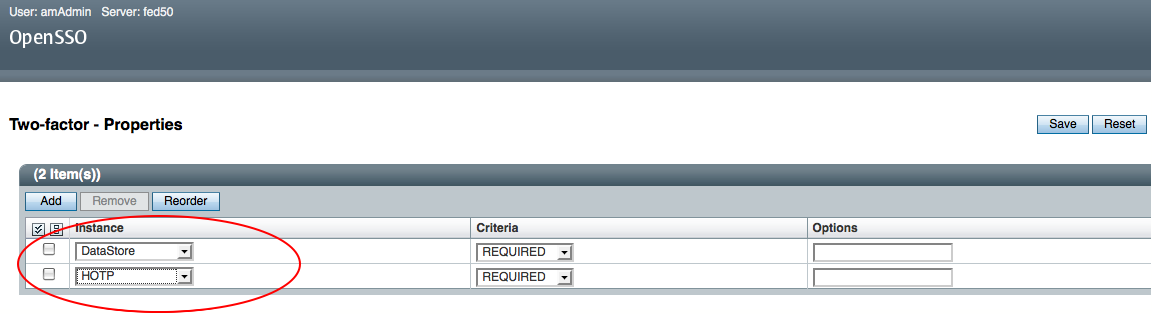
- Configure an Authentication Chain that includes HOTP authentication module with any other authentication module (ex. Datastore, LDAP). You may note HOTP authentication cannot act as primary authentication since it HOTP authentication does not identify the user profile, so it must be combined with an authentication module that identifies the calling user identity. To create an authentication chain… goto the OpenSSO administrator console, select “Access Control”, Goto “Authentication Chaining”, click on “New”, assign a name to the authentication chain (ex. Two-factor”) and the choose “HOTP” module instance and select “Required”.
-
- Now the OpenSSO One-time Authentication Module is ready for use as par of “Two-factor” authentication chain.
- Create an User Profile that identifies the user’s “Telephone Number” attribute with the Mobile Phone Number appended with the SMS Gateway domain.
- For example:
- AT&T (USA) : YourPhoneNumber@txt.att.net (178199931234@txt.att.net)
- SprintPCS : YourPhoneNumber@messaging.sprintpcs.com
- T-Mobile : YourPhoneNumber@tmomail.net
- Virgin Mobile: YourPhoneNumber@vmobl.com
- Verizon: YourPhoneNumber@vtext.com
- Metro PCS: YourPhoneNumber@MyMetroPcs.com
- For a complete list of Email to SMS Gateways refer to: http://www.mutube.com/projects/open-email-to-sms/gateway-list/
- For example:
- Test drive the configured One-time Password based SSO authentication, by accessing the URL of the configured “Two-factor” authentication chain as follows:
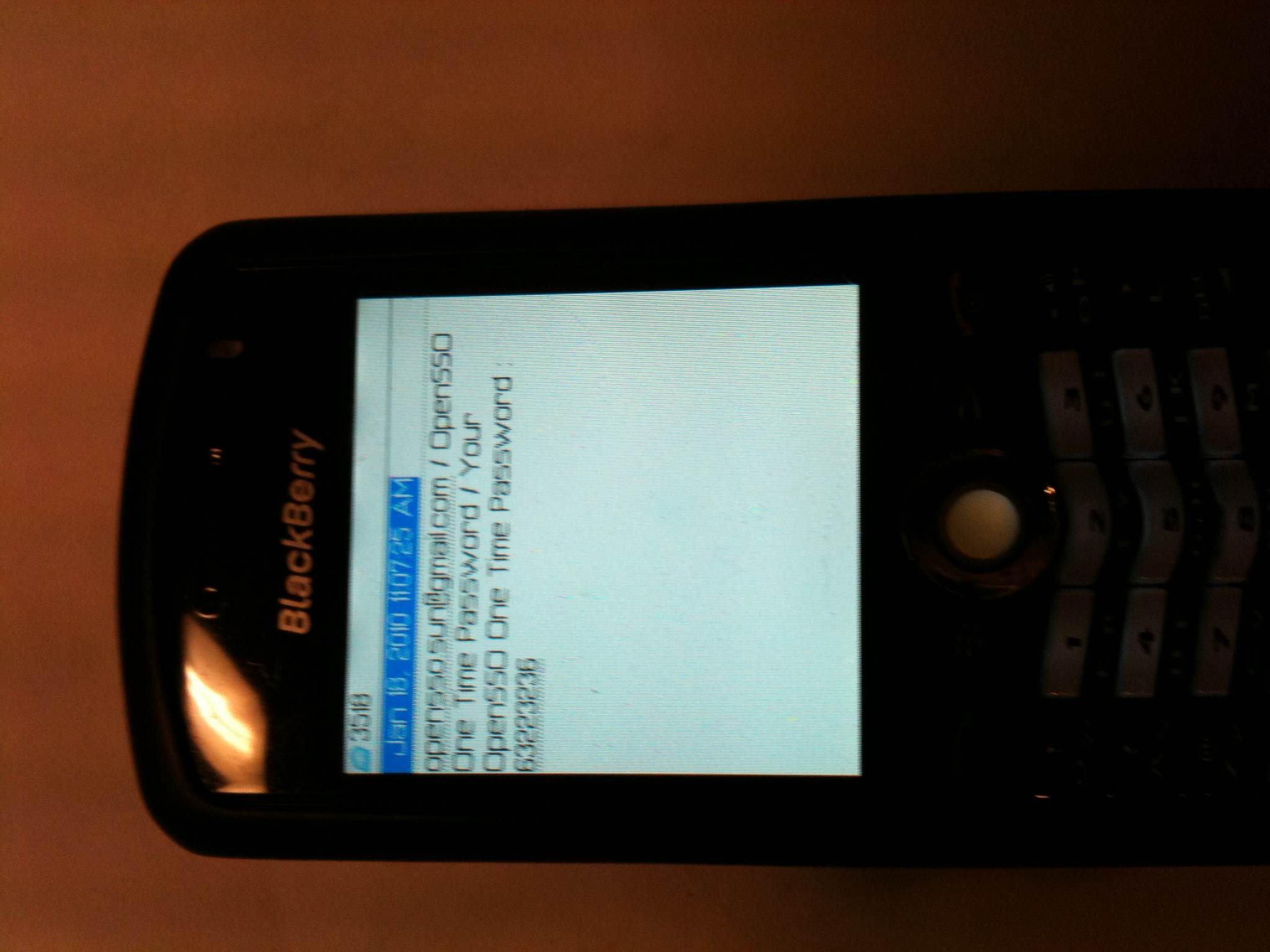
- As a result, you will be prompted to perform username/password authentication and then followed by HOTP. To deliver One-Time Password, click “Request OTP Code”, the One-time password will be delivered to your Mobile via SMS and also via email (provided in your User profile).
Adopting to One-time Pasword based authentication credentials certainly helps to defend against many illegitimate access using compromised user credentials such as Passwords, PIN and Digital certificates. Using OpenSSO based OTP authentication is just a no-brainer… try it for yourselves, I am sure you will enjoy !

Pingback: ATM Fraud and Security Digest – July 2009 | Insurance Salvage Cars
Hello,
Thanks for this article !
I’m testing this on my VM but I have a little problem, openam try to send the mail with the address opensso@sun.com and my SMTP does not allow this. Do you know how can I change this setting? I’ve searched in the admin console without success.
Thanks again,
Arnaud.
Hi again,
I’ve found what to do to change the mail.
I’ve modified the amAuthHOTP.properties and reboot the server, all works now 🙂
Hi, I am having a different issue…unlike this one… I installed OpenSSO version 8… not the express one…In which I cant see the HOTP service… I can see various other options such as (inside Configuration-> Authentication)
Active Directory,
Anonymous,
Certificate,
Core,
Data Store,
Federation,
HTTP Basic,
JDBC,
LDAP, etc etc
But I cant see the HOTP option..Could you help me out with this issue? How do I configure the HOTP? OpenSSO is not providing me that option..Do I need to execute some command or anything? After achieving Password Reset Policy Its giving me the follow message
“Your password has been reset but we are unable to send it to you. Contact your administrator.”
Thanks and Regards,
Hardi
Hi
I have configured the OTP in OpenSSO 9.5.4 . but when i complete and check the Two-Factor it shows following error
An internal authentication error has occurred.
Contact your system administrator.
Return to Login page.
Pl help ..
Hi
Thanks alot for the article.
I’m greatly interested in Java Card 3 Platform. Recently I read something in JCF that stated :
“In contrast to Java Card 2.X that the cards acts on incoming commands only, the Java Card 3 can initiate communications”
I wanted to know what this means?
Thanks again
andi